In this article, I've highlighted the 5 features which I consider to be the most helpful all around. Whether you work by yourself or on a team, these new features can save you time and improve your development experience.
1. Prototyping and Throw-Away Applications
One of the first things you may notice when starting Visual Studio 2013 is that the "New Project" window looks a bit different, as shown in figure below. When creating a new project, the location and name of the solution no longer have to be set immediately. In previous versions, the project's name and location had to be set before it was created, even if you were just testing something out and planned to delete it right away. For those who create many new projects, that meant either an extra step to delete the project or having a cluttered project directory.
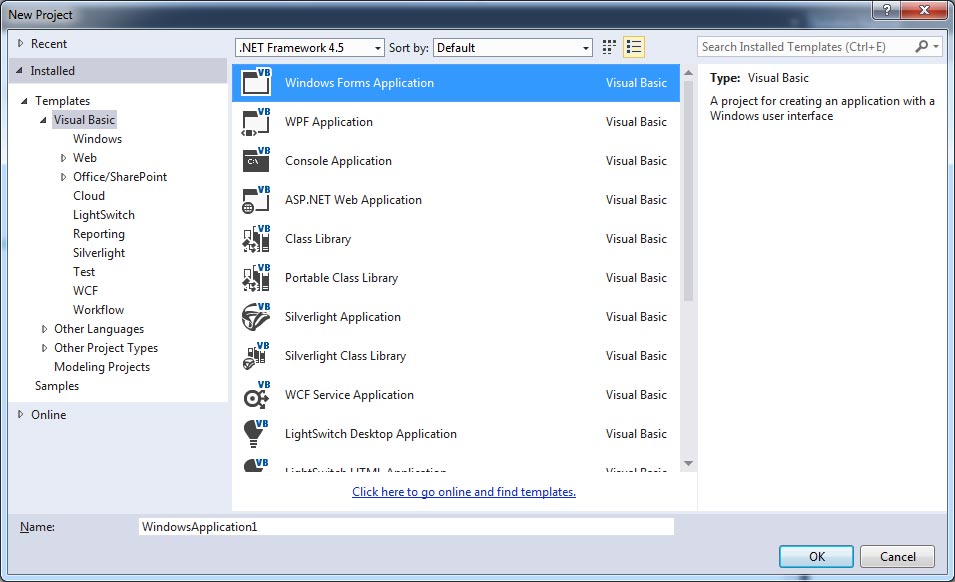
Visual Studio now works more like Microsoft Office applications, allowing you to create a project and start coding, and defer the decision of if/where to save it.
2. Peek Definitions
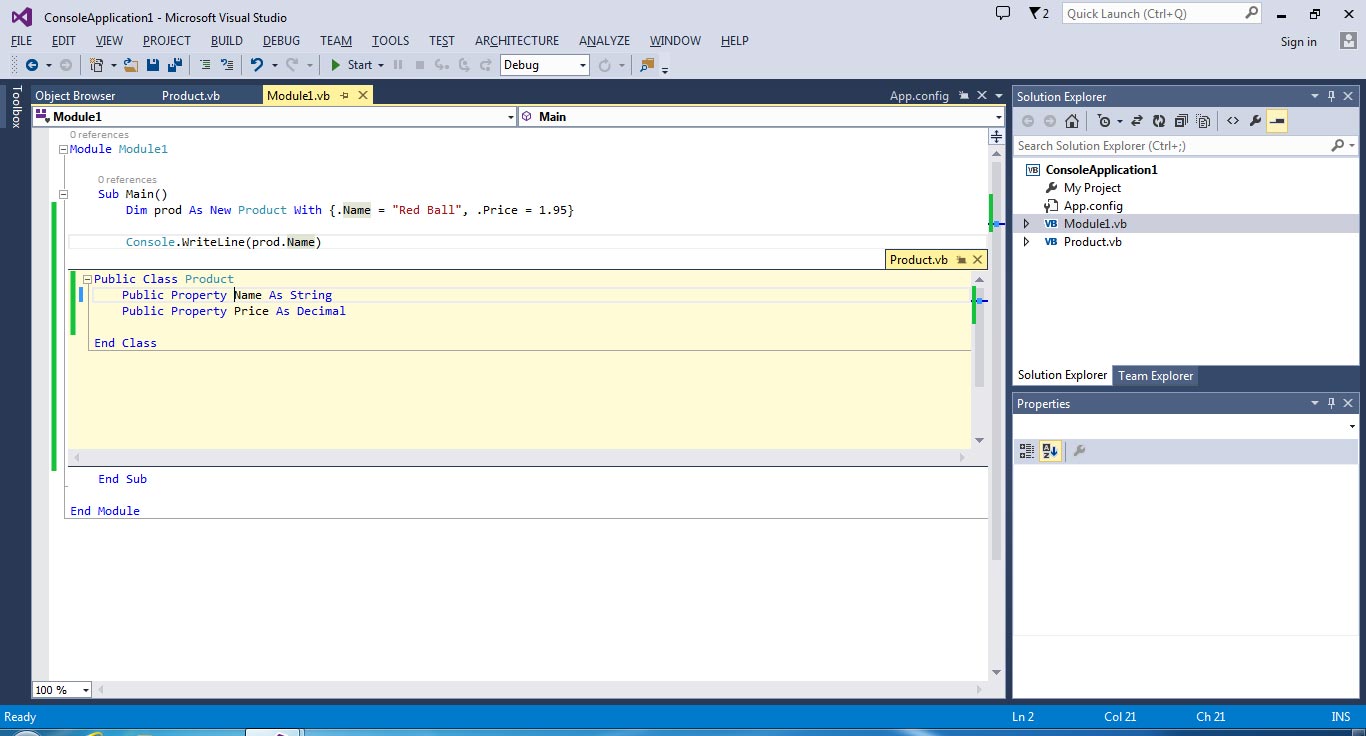
Peek Definitions lets you take a quick peek at a class or method definition without opening the file. You may be accustomed to hitting F12 to go to an object's definition, but now if you hit Alt+F12 instead, you will be able to take a peek at the definition just below its usage. As shown in figure below, I had my cursor on "prod.Name" when I hit Alt+F12, bringing up the definition of the Product class right inside my code window.
3. Improved Navigation and Search
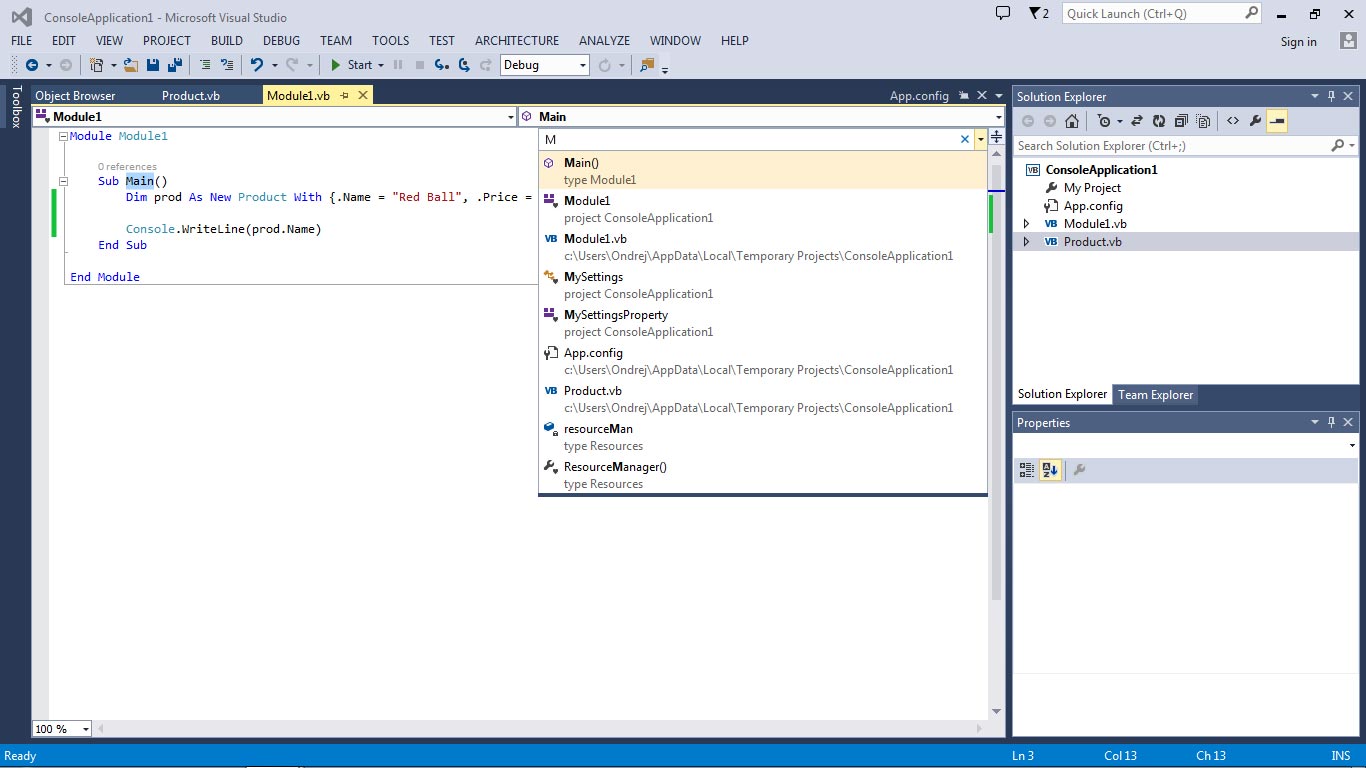
Along the lines of Peek Definitions, you can also try hitting CTRL+, which will behave differently depending on the position of your cursor. If the cursor is on a blank line, you can just start typing anything and it will begin searching for what you're typing. If the cursor is on some code, that object will be automatically typed into the search box to get you started. Take a look at figure below to see search function looks like. You can then use your arrow keys or mouse to navigate to any of the results of the search.
4. CodeLens
CodeLens is a feature that will be available only in Visual Studio Ultimate edition. By default, the number of times a property or method is referenced by your code is shown above that property or method. This information can be helpful when changing existing code, since you'll know if the method is called from many places or just a handful. In larger projects, especially ones where you're not familiar with the entire codebase, this can be a big time saver. The number of references is shown in a small font above each property or method on your class, as shown in figure below. Clicking on the number of references will show you all of the methods that call it, making it easy to find and navigate to those sections of your code.

While not shown here, CodeLens also has some nice Team Foundation Server (TFS) integration. If you're using TFS, it will allow you to see commit history and unit tests targeting the code in question.
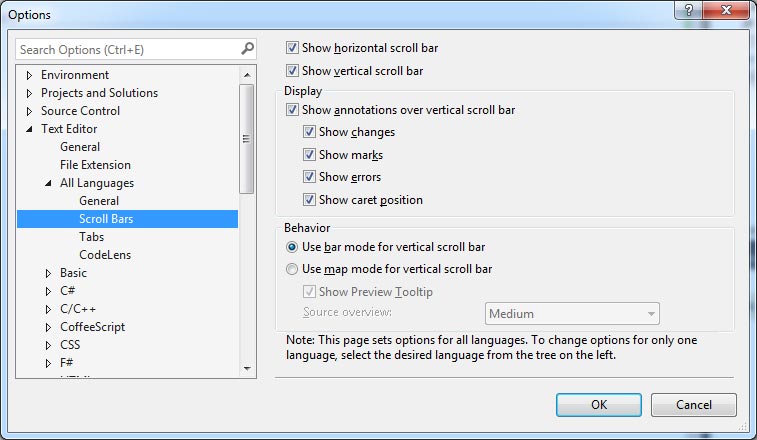
5. Scroll Bar Customization
In Visual Studio 2013, the scroll bar can now be customized to give you a better overview of large files. It can be set to show various annotations, such as changes, errors, breakpoints and more. Optionally, it can be set to "map mode," which will give you a zoomed-out representation of your code right on the scroll bar itself. The difference between bar mode (the default) and map mode can be seen in figure below.
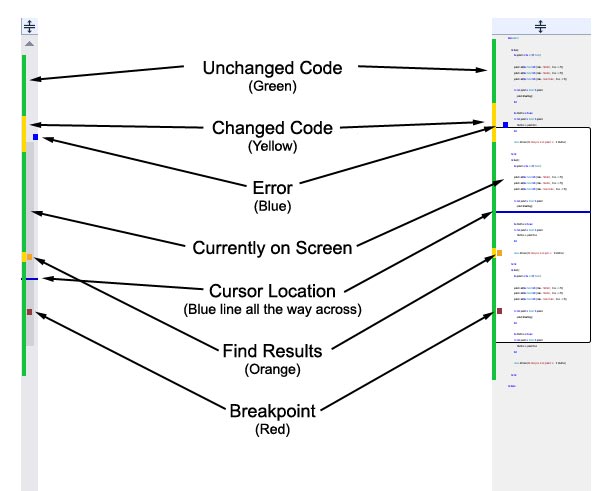
The options screen, is accessible by going to Tools > Options > Text Editor > All Languages > Scroll Bars.